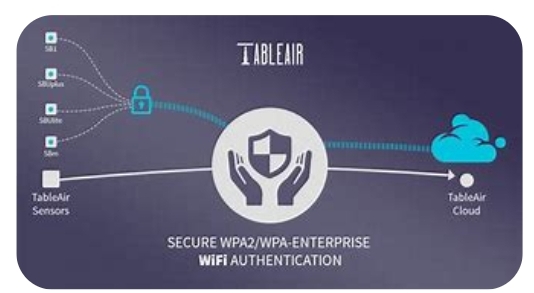
Overview of WPA Authentication
If you are new to this subject term, here we would tell you everything you need to know about Wpa, first stands for Wi-fi Protected Access. Primarily it is used to secure wireless networks. This security gateway is an improvement over the initial WEP (wired Equivalent Privacy) protocol, which has become weak and can easily be accessed by hackers. Furthermore, the WPA authentication process is a series of steps that makes sure that only the authorized users can have access to the network.
The WPA authentication process starts with the user connecting to the wireless network. The user then requests access from the access point by sending an authentication request. The access point of theWPA authentication process sends a challenge request to the user, which is a random string of characters. The user takes the challenge request, combines it with a shared secret key, and encrypts it. The encrypted response is sent back to the access point.
The access point receives the encrypted response from the user and uses its own shared secret key to decrypt it. If the decrypted response matches the challenge request, the access point knows that the user has the correct shared secret key and is authorized to access the network. The access point then sends an authentication confirmation to the user, and the user is granted access to the network.
The WPA authentication process also includes a key management mechanism. This mechanism is responsible for generating and distributing keys that are used to encrypt and decrypt data transmitted over the wireless network. The key management mechanism ensures that the keys are changed frequently and are only shared with authorized users.
WPA authentication process has several advantages over WEP. First, it provides stronger data encryption, making it more difficult for unauthorized users to hack into the network.WPA authentication process uses a more secure authentication process, making it harder for attackers to gain access to the network. Finally, it includes a key management mechanism that ensures that the network remains secure over time.
Types of WPA Authentication Process
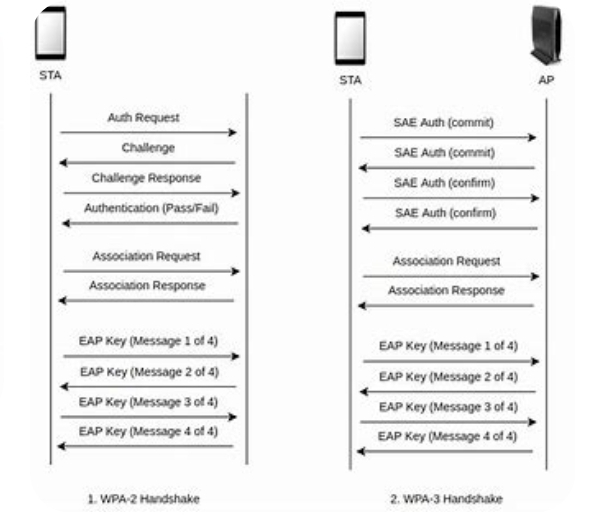
In terms of stronger security provisions WPA (wi-fi protected Access) is the best. This is because it provides stronger encryption and authentication than its predecessor, the WEP (wired Equivalent Privacy). There are two main types of WPA Authentication Methods.
- WPA-PSK (Pre-Shared Key): This is also known as WPA-Personal. It uses a passphrase or a shared key that is entered by all devices connecting to the wireless network. This method is suitable for home or small office networks with a limited number of users.
- WPA-Enterprise: This is also known as WPA2-Enterprise. It uses an 802.1X authentication server that validates the user credentials using RADIUS (Remote Authentication Dial-In User Service) protocol. This method is suitable for larger organizations with more users where each user has a unique login credential.
The two methods use the same encryption technique (AES) to protect network traffic. However, WPA-ENTERPRISE provides better authentication and limits the use of shared keys.
Pre-shared Key Authentication Process
PSK Authentication is a method of authenticating users or devices based on a shared secret key. This method is mostly used in wireless networks, virtual private networks, as well as other types of network security protocols. The authentication process involves the below-listed steps.
- Configuration of Pre-Shared Key: The PSK is first configured in the authentication server and on the client device or user.
- Client Initiation: The client device or user initiates the authentication process by sending a request to the authentication server.
- Authentication Request: The authentication server responds by sending an authentication request to the client device or user. This request includes a random number generated by the server.
- PSK Verification: The client device or user encrypts the random number with the PSK and sends it back to the authentication server.
- Authentication Response: The authentication server verifies the encrypted random number sent by the client device or user by decrypting it with the same PSK. If the decrypted value matches the original random number sent by the server, the authentication server sends an authentication response to the client device or user.
- Successful Authentication: The client device or user receives the authentication response and is deemed to have been successfully authenticated. They can now access the network resources that they are authorized to use.
802.1X Authentication Process
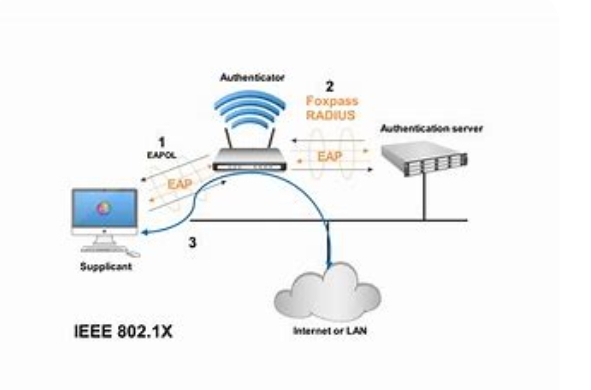
The 802.1X Authentication process is a security protocol that is used to authenticate and authorize any device trying to connect to a network. It is responsible for providing a framework for port-based network access controlled by setting up a secure communication channel between the client device and the network access control server.
Below are the authentication process
- The client device sends a request to connect to the network.
- The network access point sends a message back requesting the client’s identity.
- The client device sends its identity to the network access point.
- The network access point sends the client device a certificate request.
- The client device sends back its certificate.
- The network access point sends the client device an authentication request.
- The client device sends an encrypted challenge response.
- The network access point verifies the encrypted response and sends an authentication success message to the client device.
- The client device is allowed access to the network.
WPA2 Enterprise Authentication Process
The authentication process of the WPA2 enterprise involves the following steps.
- User Attempting to Connect: The user tries to connect to a WPA2 enterprise wireless network by selecting the SSID from their list of available networks on their device.
- IEEE 802.1X Authentication Framework: The WPA2 enterprise network uses the IEEE 802.1X authentication framework, which allows for authentication between the client and server. Once the user attempts to connect, the server (authentication server) sends a message to the client requesting their identity.
- User Identity Verification: The user enters their credentials (username and password) into the client device, which is then sent to the authentication server for verification.
- Authentication Server Verification: The authentication server verifies the user’s credentials against a database, such as Active Directory.
- Server Response: If the user’s credentials are valid, the authentication server sends a message back to the client device to authenticate the connection.
- Key Encryption: Once the connection is authenticated, the client and server use the four-way handshake to negotiate an encryption key that will be used to secure the wireless data transmission.
- Successful Connection: The client device is now successfully connected to the WPA2 enterprise network using the client-server authentication process. The encryption key is used to encrypt wireless traffic between the client and server, ensuring that the wireless network is secure.
Strengths and Weaknesses of WPA Authentication
Everything in life has both strengths and weaknesses, and WPA Authentication is not an exception. Below are the strengths and weaknesses of WPA.
Strengths:
- Cryptographic Protection: WPA uses advanced cryptographic protocols to protect the network against unauthorized access. This protection is applied to both the authentication credentials and the data transmitted over the network.
- Improved Authentication: WPA provides strong authentication mechanisms that prevent unauthorized users from accessing the network. This mechanism uses a pre-shared key (PSK) or a centralized authentication server such as RADIUS (Remote Authentication Dial In User Service) to authenticate users.
- Stronger Encryption: WPA uses the advanced encryption standard (AES) to encrypt data transmitted over the network. This encryption algorithm is highly secure and cannot be easily broken by attackers.
Weaknesses:
- Vulnerable to Attacks: WPA may be vulnerable to several attacks, including brute force attacks, dictionary attacks, and rogue access point attacks. These attacks exploit vulnerabilities in the authentication protocols to gain unauthorized access to the network.
- Limited Password Strength: When using PSK, the strength of the password used is limited to the length and complexity of the passphrase. This means that a weak passphrase can be easily cracked by attackers.
- Compatibility Issues: Not all devices are compatible with WPA. Some legacy devices only support the older and less secure WEP (Wired Equivalent Privacy) protocol. This incompatibility creates a security vulnerability for networks that support both WPA and WEP.
Best Practices for Securing WPA Authentication.
For WPA Authentication, here are some of the best practices you should be in place.
- Strong Passwords: A strong password is at least 12 characters long and includes uppercase and lowercase letters, numbers, and special characters. The more complex the password, the harder it is to crack.
- Change the SSID name: The name of your network should not contain any identifying information such as your name or address. You can use a random combination of letters and numbers for added security.
- Disable WPS: WPS (Wi-Fi Protected Setup) is a feature that allows devices to join a network easily. However, it can be exploited to gain access to your network. It is better to disable this feature.
- Use AES Encryption: Advanced Encryption Standard (AES) is currently the strongest encryption option available for WPA. Always choose AES when setting up the network.
- Keep Firmware Up-to-date: Regularly check for firmware updates for your router. These updates can fix security vulnerabilities, improve performance, and add new features.
Conclusion
In conclusion, the WPA authentication process is an essential part of securing a wireless network. It provides strong encryption and secure authentication, making it more difficult for attackers to gain unauthorized access to the network. By using WPA authentication process, organizations can ensure that their wireless networks are secure and that their data is protected.