In this our digital age, where sensitive information and personal information are at constant risk, implementing good security measures is essential. Authentication exhibits a vital role in ensuring the protection of user accounts and sensitive information. Step 2 authentication, also known as two-step or second-factor authentication, provides an extra strand of security in other to verify the identity of users. In this article, we shall explore the significance of Step 2 authentication, its various technique, implementation considerations, practical examples, and as well future trends.
What Is Step 2 Authentication Process?
Step 2 authentication process is a practice that follows the initial authentication step (Step 1) in other to provide an additional strand of security. It requires users to provide supplemental evidence to prove their identity. This process remarkably reduces the risk of unauthorized access and protects against identity theft, fraud, and information breaches. By implementing Step 2 authentication, organizations can enhance their security posture and safeguard user accounts.

Types of Step 2 Authentication process
Step 2 authentication process encompasses various strands, each offering definite advantages and as well considerations. These include:
- Knowledge-based authentication: This involves providing specific information that only the user should know, such as the PIN, password, or answers to security any questions. While this is widely used, it may be vulnerable to social engineering attacks or password-related risks.
- Possession-based authentication: These rely solely on physical objects that the user possesses, such as a hardware token, a smart card, or a mobile device. This method adds an additional strand of security by requiring the physical presence of the possession, making it difficult for unauthorized individuals to gain access.
- Inherence-based authentication: This leverages unique physical or behavioral inputs of the user, such as fingerprints, facial recognition, or voice recognition. Biometric authentication methods also offer a high level of security, as these attributes are difficult to replicate. However, privacy concerns and technical limitations should be taken into account.
Implementation of Step 2 Authentication process
In implementing the Step 2 authentication process can present some certain challenges and considerations for organizations. It is important to address the following aspects:
- Security risks and threats: Organizations must assess the potential security risks, such as phishing attacks, social engineering, or malware, and implement appropriate measures to diminish these risks.
- User experience and convenience: Balancing security with user experience is essential. Organizations should also strive to implement Step 2 authentication methods that are user friendly and convenient to encourage user adoption.
- Regulatory compliance: Depending on the industry and geographical location, organizations must ensure their Step 2 authentication processes comply with the relevant regulations and standards, such as GDPR or PCI DSS.
Best Practices for Implementing Step 2 Authentication Process
To maximize the effectiveness of the Step 2 authentication process, organizations should consider the following best practices:
- Multi-factor authentication (MFA): In Implementing MFA combines two or more Step 2 authentication processes, such as knowledge-based and possession-based authentication, for enhanced security.
- Risk-based authentication: Adopting risk-based authentication enables organizations to dynamically adjust the level of authentication required based on risk factors, such as user behavior, location, or transaction value.
- User education and awareness: Educating users about the importance of the Step 2 authentication process and raising awareness about potential security threats also helps to promote a security-conscious culture.
Examples of Step 2 Authentication in Practice
Step 2 authentication process, is widely in work in various industries so as to safeguard user accounts and sensitive information. Let’s explore a few practical examples:

- Online banking systems: The online banking platforms often employ Step 2 authentication factors, such as sending a one-time password (OTP) to the user’s registered mobile device, to confirm transactions and protect against unauthorized access.
- Cloud-based services: Cloud service providers always offer Step 2 authentication as an additional security measure in other to protect users’ cloud storage and sensitive information. This can include methods like authenticator apps or hardware tokens.
- E-commerce platforms: To ensure secure transactions, e-commerce platforms frequently integrate Step 2 authentication methods, such as OTPs or biometric authentication, during the checkout process.
Future Trends and Innovations in Step 2 Authentication Process
As the field of the Step 2 authentication process continues to evolve, driven by progressiveness in technology and emerging trends. Some notable future trends include:
- Biometric advancements: Ongoing evolution in facial recognition, fingerprint scanning, and other biometric technologies will continue to enhance the accuracy and security of the Step 2 authentication processes.
- Behavioral analytics and machine learning: Leveraging on machine learning algorithms and behavioral analytics, organizations can always analyze user behavior patterns to detect anomalies and potential security threats, enabling more effective Step 2 authentication.
- Passwordless authentication: Passwordless authentication methods, such as token-based or biometric-based approaches, are gaining traction, eliminating the need for traditional passwords and as well enhancing security.
Why is Step 2 authentication necessary?
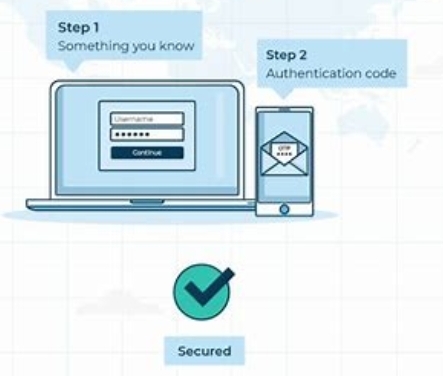
Step 2 authentication adds an additional strand of security to protect against unauthorized access, identity theft, and information breaches. It also reduces the risk of relying solely on passwords or knowledge-based authentication, which can as well be vulnerable to various attacks.
How does Step 2 authentication improve security?
Step 2 authentication improves security by requiring it users to provide an additional evidence of their identity, making it more difficult for unauthorized individuals to gain access. It adds an extra strand of protection in case the initial authentication step is compromised.
Is Step 2 authentication mandatory?
Step 2 authentication is not always mandatory, but it is highly recommended to enhance security, especially for sensitive accounts or systems. Many online platforms and service providers offer the Step 2 authentication as an optional feature for users to enable.
Is Step 2 authentication inconvenient for users?
While Step 2 authentication adds an additional step to the login process, the inconvenience is outweighed by the increased security it provides. However, organizations should also strive to implement user-friendly methods and educate users about the significance of this security measure to encourage adoption.
Can Step 2 authentication be used for all types of accounts?
Yes, the step 2 authentication can be implemented for a wide range of accounts, including email, social media, banking, and online shopping accounts. The availability of this feature may depend on the platform or service provider.
Are there any alternatives to Step 2 authentication?
Yes, there are alternative authentication methods, such as Step 1 authentication (single-factor authentication), which relies solely on passwords or knowledge-based factors. Nevertheless, the Step 2 authentication process is widely recommended as it significantly enhances data security by requiring an additional form of verification. Other alternatives include advanced methods like biometric authentication or passwordless authentication, which eliminate the need for traditional passwords altogether.
In Summary
The Step 2 authentication process is an essential component of a robust security framework. By implementing the Step 2 authentication process, organizations can significantly enhance the protection of user accounts,sensitive data, and mitigate the risk of unauthorized access. It is crucial for organizations to stay updated with the latest trends and innovations in the Step 2 authentication process to maintain a strong security posture in the ever-evolving digital landscape.