If you are new to the context, 802.1x authentication is among the security protocols that is deployed in computer networks and wireless networks, this makes it possible for only the authorized user to have access to such network and resources.
802.1x authentication method provides an extra layer of security to the traditional network authentication methods which includes biometrics and password.
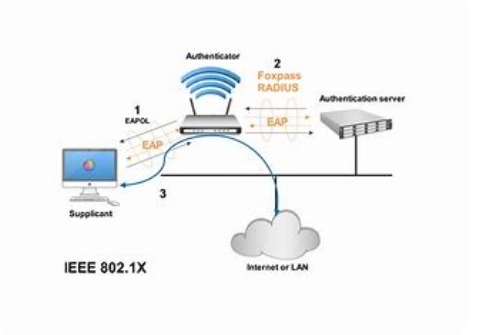
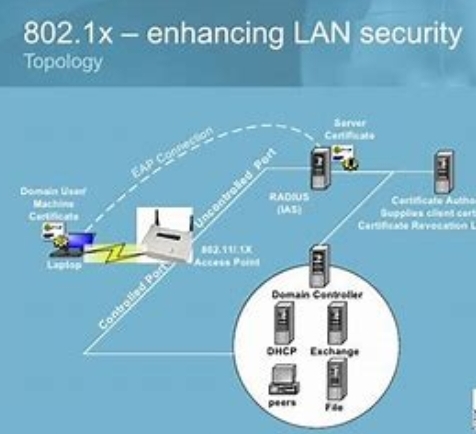
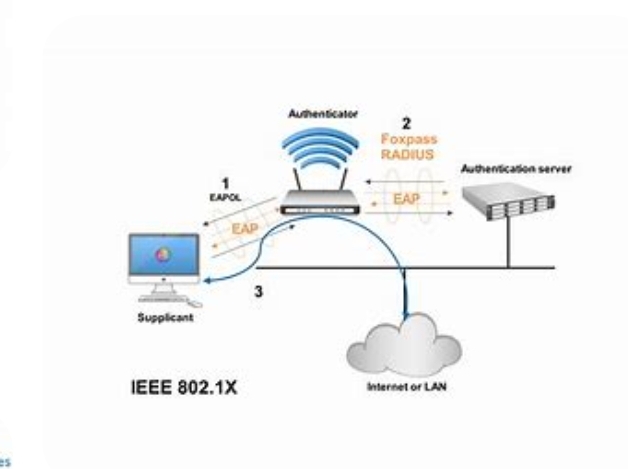
The 802.1x authentication procedure includes 3 most important entities: the supplicant, the authenticator, and the authentication server. The supplicant is the tool or consumer that wants to hook up with the network, the authenticator is the network tool that controls entry to the network, and the authentication server is the entity that authenticates the user or device and determines if it is authorized to get admission to the network.
The technique of 802.1x authentication begins with the supplicant sending its credentials (such as a username and password) to the authenticator. The authenticator then encapsulates the credentials in an Extensible Authentication Protocol (EAP) frame and sends it to the authentication server. The authentication server validates the credentials and sends a response returned to the authenticator indicating whether the credentials are valid or not.
If the credentials are legitimate, the authenticator lets in the supplicant to get admission to the community. If the credentials are invalid or if the authentication server does no longer reply, the authenticator denies access to the community. This manner is repeated on every occasion the tool or consumer tries to connect to the community.
802.1x authentication is utilized in a huge variety of programs, together with stressed out networks, wi-fi networks, and far off access networks. It presents a high degree of safety and allows protection against unauthorized access to sensitive community sources.
Benefits of using 802.1x authentication method
802.1x authentication method offers several benefits and advantages those benefits may include:
- improving network safety – The number one gain of the usage of 802.1x authentication is that it complements community security by means of requiring users to offer valid credentials before getting access to the community. This prevents unauthorized users from having access to the network and sensitive records.
- Decreasing network Overhead – 802.1x permits for efficient management of network sources, which include bandwidth, via allowing simplest authenticated customers to get admission to the network. This limits the number of customers and devices in the community, reducing community congestion and improving community performance.
- stopping Unauthorized get admission to – 802.1x authentication guarantees that most effective authorized customers can access the community, stopping unauthorized gadgets from connecting. This prevents capacity security breaches and cyber-assaults on the community.
- permitting policy Enforcement – 802.1x authentication permits for community administrators to put in force network guidelines and restrictions, which includes restricting get right of entry to to sure sources or setting time constraints on community get admission to. This gives more control over network utilization and safety.
- Centralized network management – 802.1x authentication presents a centralized manner of handling community get entry, simplifying network management. Community directors can effortlessly authenticate and control devices from a critical place.
Understanding the components of 802.1x authentication
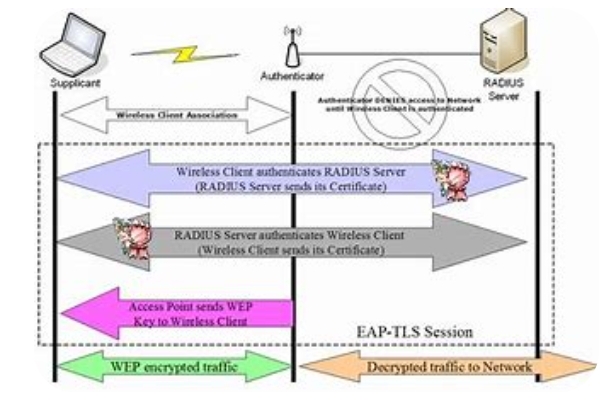
For you to understand the 802.1x authentication method it is very important to also study the major components of the security gateway. 802.1x authentication has three major components which is namely:
- Supplicant: The supplicant is the consumer tool that needs access to the community. it may be a laptop, telephone or any community-enabled device. The supplicant initiates the authentication procedure and gives its credentials to the authenticator.
- Authenticator: The authenticator is the network device that gives access to the network. it could be a switch, wi-fi access point or router. The authenticator acts as a middleman among the supplicant and the authentication server. It receives the credentials from the supplicant and forwards them to the authentication server for verification. If the credentials are valid, the authenticator lets in to get entry to the network.
- Authentication server: The authentication server is responsible for verifying the credentials of the supplicant. It could be a remote Authentication Dial-In user provider (RADIUS) server or lightweight Listing Access Protocol (LDAP) server. The authentication server receives the credentials forwarded via the authenticator and verifies them towards its database. If the credentials are valid, the authentication server sends a message to the authenticator permitting access to the network.
Types of methods used in 802.1x authentication.
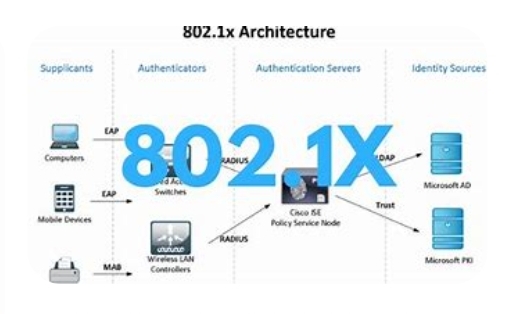
There are several methods used in setting up the 802.1 authentication, here are some of the most used ones.
1. EAP-TLS (Transport Layer Security): This method provides mutual authentication between the client and the server, with certificates used for authentication.
2. EAP-TTLS (Tunneled Transport Layer Security): This method creates a secure tunnel between the client and the server, with EAP methods used for authentication.
3. PEAP (Protected Extensible Authentication Protocol): This method uses a secure tunnel established by TLS to authenticate the client with EAP methods.
4. EAP-FAST (Flexible Authentication via Secure Tunneling): This method creates a secure tunnel between the client and the server, using a pre-shared key to authenticate the client.
5. EAP-SIM (Subscriber Identity Module): This method uses the SIM card in a mobile device for authentication.
6. EAP-MD5 (Message Digest 5): This method uses a shared secret, or password, to authenticate the client.
7. EAP-GTC (Generic Token Card): This method uses a token, such as a smart card, USB key, or hardware token for authentication.
8. EAP-TLS-Cert (Certificate-Based Transport Layer Security): This method is a variant of EAP-TLS that relies on X.509 certificates to provide mutual authentication between the client and the server.
How to set up and configure 802.1x authentication
By following all the step identified below you will successfully configure your 802.1x authentication protocol.
- Identify your network infrastructure: Before you start configuring 802.1x authentication, you need to identify your network’s infrastructure. You should have an authentication server, such as RADIUS or Active Directory, and an access control device, such as a switch or wireless access point.
- Configure the authentication server: The authentication server is responsible for verifying user credentials. Configure the authentication server by creating user accounts and specifying the authentication method, such as PEAP or EAP-TLS.
- Configure the access control device: The access control device is responsible for enforcing access policies. Configure the access control device by enabling 802.1x authentication and specifying the authentication server’s IP address and port number.
- Create network access policies: Network access policies define the rules for granting or denying access to network resources. Create policies based on user or device identity, network location, or time of day.
- Test and troubleshoot: After configuring 802.1x authentication, you should test the network to ensure that users can authenticate successfully. If there are any issues, troubleshoot by reviewing log files and error messages, and make appropriate changes to the configuration.
Limitations and challenges of 802.1x authentication.
802.1x authentication has its limitations and challenges, but it remains a popular and effective means of securing network access. Network administrators must be aware of these limitations and challenges to ensure the successful deployment and operation of 802.1x authentication.
1. Compatibility: One of the major limitations of 802.1x is that it requires the network devices and endpoints to be compliant with the protocol. If the hardware or software does not support 802.1x, then the authentication will fail, and users will not be able to access the network.
2. Configuration complexity: Configuring 802.1x authentication can be challenging, especially for larger networks. Network administrators need to configure each network device and endpoint with the correct settings to ensure proper authentication.
3. Certificate management: 802.1x uses digital certificates to authenticate network devices and endpoints. Managing these certificates can be a daunting task, especially in large networks with many devices and users.
4. User experience: From a user’s perspective, 802.1x authentication can be confusing and frustrating. Users may need to enter their credentials multiple times or encounter errors, which can slow down their access to the network.
5. Security risks: While 802.1x provides robust security, it is not immune to attacks. Hackers can attempt to exploit vulnerabilities in the authentication process and gain unauthorized access to the network.
6. Limited scalability: 802.1x authentication is well-suited for smaller networks, but it may not be scalable for larger networks that require a significant amount of user and device authentication.
Implementing 802.1x authentication in enterprise networks
We have sunmerized the steps involved in implementing 802.1x authentication in enterprise networks.
- Step 1: Define network access policies: Before implementing 802.1x authentication, you need to define the network access policies that will determine which users and devices are allowed to access the network. For example, you can create policies that grant access to employees, deny access to guests, and require additional authentication for sensitive data.
- Step 2: Configure network devices: 802.1x authentication is supported by most network devices, including switches and wireless access points. You need to configure the devices to enforce the access policies you defined in step 1. For example, you can configure switches to block access for devices that fail authentication or allow access with limited privileges for guests.
- Step 3: Configure authentication servers: 802.1x authentication requires a backend authentication server, such as a RADIUS server, to authenticate the users and devices trying to access the network. You need to configure the authentication server to store the credentials of users and devices and authenticate them during the authentication process.
- Step 4: Configure clients
To authenticate with the network, clients need to be configured with the necessary settings, such as the SSID and authentication type. This can be done manually or using an automated tool like Group Policy.
- Step 5: Monitor the network: Once 802.1x authentication is implemented, you need to monitor the network to ensure that it is working properly. You can use tools like network monitoring software to track network access and identify any unauthorized access attempts.
Comparison of 802.1x authentication method with other authentication methods
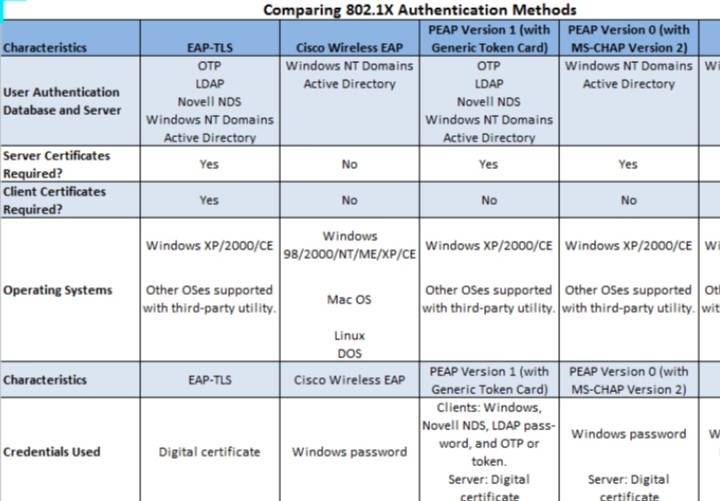
Here’s a comparison of 802.1x authentication method with other authentication methods:
1. Password-based authentication: Password-based authentication is the most commonly used authentication method. It requires a user ID and password to access the network. 802.1x authentication is more secure as it uses a combination of user ID and password or a digital certificate.
2. Biometric authentication: Biometric authentication uses physical features such as fingerprints, facial recognition, or iris scans to authenticate access requests. Biometric authentication is more reliable and secure than password-based authentication; however, it is expensive to implement and can be difficult to maintain.
3. Token-based authentication: Token-based authentication requires a physical device, such as a smart card or USB stick, to authenticate access requests. Token-based authentication provides better security compared to password-based authentication as it requires something physical in addition to a password. However, tokens can be expensive, and the user has to carry them around all the time.
4. Kerberos authentication: Kerberos is a widely used authentication method that uses a centralized authentication server to verify access requests. Kerberos authentication provides better security than password-based authentication, but it is more complicated to set up and manage.
Best practices for securing the network with 802.1x authentication.
If you are using 802.1x authentication method here are the best practices that you should put in place in order to secure the network from hackers.
1. Use strong authentication protocols: Implement strong authentication protocols, such as EAP-TLS or PEAP, to ensure the network is only accessible to authorized users.
2. Deploy certificates: Deploy digital certificates to authenticate users and devices on the network. This will ensure that only authorized devices can access sensitive data.
3. Use VLAN tagging: Implement VLAN tagging to segregate network traffic and limit access to certain network resources.
4. Enable port security: Enable port security to limit access to specific ports on the network. Set limits on the number of devices that can connect to each port to prevent unauthorized access.
5. Use NAC solutions: Consider implementing network access control (NAC) solutions to monitor network activity and restrict access to unauthorized users.
6. Regularly update security policies: Regularly update security policies to ensure they align with changing security threats and business needs. This will help prevent unauthorized access and data breaches.
7. Configure network devices securely: Ensure network devices, such as routers and firewalls, are configured securely and use strong encryption to protect sensitive data.
8. Monitor network activity: Regularly monitor network activity to identify suspicious behavior and potential security threats. Use intrusion detection and prevention systems to detect and respond to threats in real-time.
9. Provide regular security awareness training: Provide regular security awareness training to employees to educate them on best practices for securing the network and staying vigilant against security threats.
10. Conduct regular vulnerability assessments: Conduct regular vulnerability assessments to identify potential security weaknesses in the network and address them promptly.
The future of 802.1x authentication method.
802.1x authentication has been widely used in network security for decades. As technology advances, there are several possible future scenarios for this authentication method in networking. Here are some expectations:
1. Increased use of biometric authentication: Biometric authentication, such as facial recognition or fingerprint scanning, is becoming more prevalent in modern authentication. It is possible that future 802.1x authentication will incorporate biometric authentication as a secure and convenient way to identify users.
2. Augmented Reality (AR) and Virtual Reality (VR) authentication: AR and VR technologies are becoming more prevalent in the workplace. There could be a future where users are authenticated using AR or VR technologies.
3. Blockchain authentication: Blockchain technology provides an immutable record of transactions that can be used for authentication purposes. Future 802.1x authentication may leverage blockchain technology to provide a secure and transparent way to authenticate users.
4. Quantum-resistant authentication: As quantum computing advances, traditional encryption methods may become more vulnerable to attack. Future 802.1x authentication could implement quantum-resistant authentication methods to ensure the security of network authentication in the age of quantum computing.
5. Increased use of Artificial Intelligence (AI) and Machine Learning (ML) authentication: AI and ML technologies can analyze vast amounts of data to identify patterns and anomalies. Future 802.1x authentication could incorporate AI and ML to monitor and identify potential threats in real-time, thus strengthening network security.
Conclusion
In summary, 802.1x authentication is a framework for network access control that provides port-based access control by authenticating devices that are trying to connect to a network. It is commonly used in wired and wireless networks and provides a way for administrators to grant or deny network access based on the authenticated identity of the user or the device.
In 802.1x authentication, a device trying to connect to a network is first challenged for its identity by the authenticated device. The authentication process involves a three-way handshake between the supplicant (the device requesting access), the authenticator (the network hardware interface that controls access to the network), and the authentication server (the backend server that verifies the identity of the device or user requesting access).
Overall, 802.1x authentication provides a secure way to control network access by requiring authentication from devices and users before granting network access. It enhances network security by preventing unauthorized access and ensuring that only authorized devices and users can connect to a network.
FAQs
In this section we will be answering some of the questions regarding to 802.1x authentication method. If you have futher questions that you want us to answer kindly send us message through our email in the contact us section.
What is 802.1 authentication method?
802.1 authentication method is a set of standards defined by the Institute of Electrical and Electronics Engineers (IEEE) that provide a framework for network access control. This method is also known as IEEE 802.1X or just 802.1X.
It allows for secure authentication and authorization of devices trying to connect to a network, and controls their access to resources and services within that network. This is accomplished through a combination of authentication servers, access points, and clients, with each device and user requiring credentials to authenticate.
How does 802.1 authentication work?
802.1 authentication is a network security protocol that helps to ensure secure communication between devices on the network. It works by using a combination of authentication methods, such as passwords, certificates or biometrics, to verify the identity of a device before allowing it to connect to the network.
When a device attempts to connect to the network, it sends an authentication request to the authentication server. The server then verifies the identity of the device by asking it to provide some proof of identity, such as a password. If the device is able to provide the correct identity token, the authentication server grants it access to the network. If not, the device is denied access and cannot connect to the network.
This process helps to ensure that only authorized devices are able to connect to the network, preventing unauthorized access and potential security breaches. 802.1 authentication is commonly used in enterprise networks, where security is a top priority.
Which devices support 802.1 authentication?
Most modern network devices, such as routers, switches, access points, and firewalls, support 802.1x authentication. Additionally, many operating systems, such as Windows, macOS, and Linux, support 802.1x authentication for wired and wireless connections. Some smartphones and tablets also support 802.1x authentication for secure Wi-Fi connections.
Are there any security concerns with 802.1 authentication?
Yes, there are security concerns with 802.1 authentication. Some of the security concerns include:
1) Weak Passwords: If the authentication is based on passwords, weak passwords can be easily cracked by hackers, leading to unauthorized access.
2) Man-in-the-Middle Attacks: 802.1 authentication does not provide protection against man-in-the-middle attacks. An attacker can intercept the authentication messages and compromise the authentication process.
3) Eavesdropping: Authentication messages sent over the network can be intercepted by hackers. This can lead to the disclosure of sensitive information such as usernames and passwords.
4) Credential Theft: If the authentication method involves storing credentials, a hacker can steal the credentials and use them to gain unauthorized access.
5) DoS Attacks: 802.1 authentication is susceptible to denial-of-service (DoS) attacks, where an attacker floods the authentication server with requests, causing it to crash or deny service to legitimate users.
To address these security concerns, it is recommended to use strong authentication methods that incorporate encryption, such as EAP-TLS or EAP-PEAP. Additionally, implementing network access control (NAC) solutions can provide a layered approach to network security and mitigate the risks associated with 802.1 authentication.






