In our progressively digital world, guaranteeing the security of our personal data has become paramount. One of the modus operandi that has gained significant recognition is the two factor authentication (2FA). With cyber threats on the increase, implementing the two factor authentication has become a critical step in safeguarding our online identities and sensitive data.
What Is Two Factor Authentication
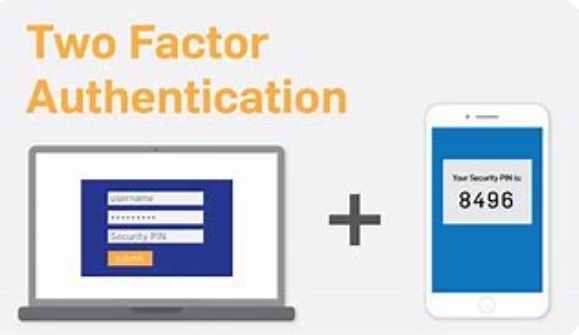
Two factor authentication involves the used of two different authentication strands to verify the user’s identity. These strands falls into three different categories: like something the end user knows (e.g. identification), something the end user has (e.g. a mobile device), and something the end user is (e.g.biometric traits). By combining multiple strands, two factor authentication significantly strengthens the security of our digital interactions.
Types of Two Factor Authentication Methods
We have various strands utilized in 2FA in other to provide an external layer of security. One of the common applications is the use of One-Time Passwords (OTPs), which are often time-limited and always generated either through a mobile app (Time-based OTP) or sent via SMS or email. Push notifications to trusted devices are also sometimes widely used, where users receive a notification and approve or deny access. Biometric authentication, such as fingerprint or face recognition, offers an appropriate and secure way to validate ones identity.
Implementing Two Factor Authentication
In other, for you to implement two factor authentication successfully, one needs to consider several strands. User acceptance and signing-up processes should be well-organized and user-friendly. Integrating with other existing systems and applications is very important for a friendly user experience. Balancing security measures with user conveniences is vital to encouraging adoption. Not forgetting, implementing best practices such as protecting the authentication strands, monitoring for any fraudulent attempts, and regular system updates are important for robust security.
Benefits and Challenges of Two Factor Authentication
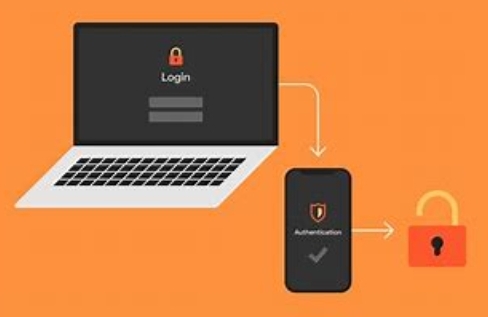
The benefits of implementing 2FA are essential. Two factor authentication provides increased security by adding an additional layer of protection against unauthorized access. It reduces the risks associated with weak passwords and password reuse. In explaining further, 2FA helps organizations and financial institutes comply with regulatory requirements. Nevertheless, challenges do exist, including user resistance and adoption hurdles, implementation costs, and potential usability and accessibility issues that must be addressed accordingly.
Examples Of Two Factor Authentication
Many organizations and financial institutes have successfully implemented 2FA In other to enhance their security architecture. For example, one of the leading banking institutions implemented 2FA through a mobile app, resulting in a significant reduction in account breaches and unauthorized access. This success story alone demonstrates how 2FA can safeguard sensitive financial information and customer trust effectively.
Future Trends and Developments in Two Factor Authentication
As technology keeps progressing, the future of 2FA holds promising advancement. Further advancements in biometric authentication, such as retina scanning and voice recognition, will also offer enhanced security. Integrating emerging technologies like blockchain and artificial intelligence will provide additional layers of protection and convenience, making authentication more secure and as well user-friendly.
Read more: WordPress security: do I need a WordPress security plugin?
Two Factor Authentication And How To Enable It
The two factor authentication (2FA) adds an additional layer of security to your accounts by requiring two verification forms during the login process. Here’s how to enable 2FA:
- Identify the platform or service: Determine which platform or service you want to enable 2FA for. Common examples include email providers (e.g., Gmail, Outlook), social media platforms (e.g., Facebook, Twitter), and online banking services.
- Go to account settings or security settings: Once you’ve identified the platform, navigate to your account settings or security settings. Look for options related to authentication or security.
- Enable Two-Factor Authentication: In the security settings, locate the option to enable Two-Factor Authentication. It may be referred to as “2FA,” “Two-Step Verification,” or a similar term.
- Choose the second factor: Select the second factor you want to use for authentication. Common options include:
- SMS or Text Message: You will receive a unique code via SMS or text message to enter during the login process.
- Authentication App: Download and install an authentication app (e.g., Google Authenticator, Authy) on your mobile device. The app generates time-based one-time codes (TOTPs) for authentication.
- Email Verification: An email with a verification code will be sent to your registered email address.
- Hardware Token: Some services offer physical devices or tokens that generate unique codes for authentication.
- Follow the setup instructions: Depending on the chosen second factor, you will be guided through the setup process. This may involve scanning a QR code with an authentication app, entering your phone number for SMS verification, or registering a hardware token.
- Verify and save backup codes: As a precaution, most services provide backup codes that can be used if you lose access to your second factor. Make sure to save these codes in a secure location.
- Test the setup: Once enabled, log out of your account and attempt to log back in. The platform should prompt you to enter the verification code from your chosen second factor.
- Keep your 2FA secure: Remember to keep your second factor secure. If using an authentication app, ensure your device is protected with a strong passcode or biometric authentication.
By enabling this two factor authentication, you have significantly enhanced the security of your accounts, thereby protecting them from unauthorized access and potential future data breaches. It is recommended to enable 2FA on all platforms and services that support it for optimal security.
Two Factor Authentication and WordPress
The two factor authentication (2FA) can be implemented on WordPress websites to enhance the security of user logins. Here’s how you can enable 2FA on a WordPress site:

- Install a 2FA plugin: You start by installing a 2FA plugin from the WordPress plugin repository. There are several popular options available, such as “Two-Factor” by Plugin Contributors or “Google Authenticator – Two-Factor Authentication” by miniOrange.
- Activate the plugin: After you’re done installing the 2FA plugin, activate it from the WordPress dashboard’s “Plugins” section.
- Configure the plugin: Once its activated, navigate to the plugin’s settings page. This can usually be found under “Settings” or “Two-Factor Authentication” in the WordPress dashboard.
- Choose an authentication method: Then select the desired authentication method for 2FA. The most common options are:
- Time-based One-Time Password (TOTP): This method involves using your mobile app such as Google Authenticator or Authy to generate temporary codes.
- Email-based authentication: A unique code is sent to your email address during the login process.
- Set up the authentication method: You will then Follow the instructions provided by the plugin to set up the chosen authentication method. For TOTP, you may actually need to scan a QR code or manually enter a code into the authentication app. For email-based authentication, provide the necessary information and configuration settings.
- Configure backup options: Some 2FA plugins also offer backup methods in case the primary authentication method is unavailable. Also, set up backup options such as backup codes or alternative email addresses.
- Customize the settings: Depending on the plugin, you may have additional settings to configure. This can include settings related to the login flow, user roles, and enforcement of 2FA.
- Test the setup: Log out of your WordPress account and attempt to log back in. You should now be prompted to enter the 2FA code from your chosen method.
By enabling 2FA on your WordPress website, you add an extra layer of security to protect user accounts from unauthorized access. It is recommended to educate your users about the importance of 2FA and encourage them to enable it for their individual accounts.
Read more: How To Keep Your Wi-Fi Safe With Wpa Authentication Process
Two Factor Authentication and iCloud
The two factor Authentication (2FA) is also available for Apple’s iCloud service and is highly recommended for securing your iCloud account. Here’s how you enable 2FA for iCloud:

- Ensure device compatibility: Before you begin enabling 2FA, make sure you have an Apple device running iOS 9 or later, macOS El Capitan or later, or watchOS 2 or later.
- On your iPhone, iPad, or iPod touch:
- Go to your “Settings” and tap on your name at the top.
- Select your “Password & Security” or “Apple ID > Password & Security.”
- Tap on “Turn On Two-Factor Authentication.”
- On your Mac:
- Click on your App n,/.le menu and select “System Preferences.”
- Choose “Apple ID” and click on “Password & Security.”
- Click on “Turn On Two-Factor Authentication.”
- Follow the on-screen instructions: Apple will guide you through the process of enabling 2FA. This includes verifying your identity, confirming your trusted phone number, and setting up a trusted device.
- Generate verification codes: During the setup process, Apple will provide you with verification codes. These codes can be used as backup options if you can’t access your trusted devices or trusted phone number.
- Complete the setup: Once you’ve followed the instructions and verified your identity, 2FA will be enabled for your iCloud account. You will now be required to enter a verification code in addition to your password when signing in to your iCloud account on a new device or browser.
- Manage your trusted devices: To manage your trusted devices, go to “Settings” or “System Preferences” > [Your Name] > “Password & Security” > “Manage Trusted Devices.” From there, you can add or remove devices.
By enabling 2FA for your iCloud account, you add an extra coating of security to protect your personal data, photos, documents, and other information stored in iCloud. It helps prevent unauthorized access and provides an additional level of verification for signing in to your iCloud account from new devices.
Two Factor Authentication vs mfa
The two factor authentication (2FA) and Multi-Factor Authentication (MFA) are both security measures that involve using multiple factors to verify it user’s identity. Nevertheless, there is a subtle difference between the two:
The two factor authentication (2FA): These require the use of two different strands for authentication. Typically, these strands fall into three different categories: something the user knows (e.g a password), something the user has (e.g mobile device), or something the user is (e.g., biometric traits). By combining two of these strands, 2FA adds an extra coating of security to the authentication process. For instance, a user may enter their password (something they know) and then receive a one-time code on their mobile device (something they have) to complete the authentication.
The Multi-Factor Authentication (MFA): As the name suggests, goes beyond two factors and involves the use of three or more strands for authentication. In addition to the factors used in 2FA, MFA can also include additional strands such as location-based verification, voice recognition, or security questions. The specific combination of strands depends on the implementation and the level of security required. MFA provides an even higher level of security compared to the 2FA by adding more coating of verification.
Two factor Authentication vs SSO
The two factor authentication (2FA) and Single Sign-On (SSO) are both security mechanisms used in protecting user accounts and enhancing convenience. Nevertheless, they serve different purposes:
Two Factor Authentication (2FA): These involve users to adds an extra coating of security to the authentication process by requiring users to provide two different types of verification. This involves combining something the user knows (e.g.password) with something the user has (e.g.mobile device). 2FA helps protect against unauthorized access even when passwords are compromised, as the attacker would still need the second factor to gain access. It is primarily focused on improving the security of individual accounts.
Single Sign-On (SSO): This is a mechanism that allows users to access multiple systems or applications with a single set of credentials. With SSO, users authenticate themselves once, just with a username and password, and then gain access to multiple resources without the need to re-enter credentials for each separate system. SSO enhances user convenience by reducing the number of login prompts and simplifying the authentication process across different applications. It is primarily focused on improving user experience and productivity.
While 2FA and SSO can work together, they serve different purposes:
- 2FA provides an additional coating of security by requiring multiple factors for authentication, regardless of whether SSO is used or not. It can be implemented as an additional security measure within an SSO environment.
- SSO simplifies the login process by allowing users to authenticate once and access multiple applications without re-entering credentials. However, SSO alone does not provide the same level of security as 2FA. Therefore, combining SSO with 2FA can provide both convenience and enhanced security.
In summary, the Two Factor Authentication (2FA) focuses on strengthening individual account security by requiring multiple factors for authentication, while Single Sign-On (SSO) streamlines the login process across multiple applications. Both measures have their own benefits, and using 2FA within an SSO environment can provide an optimal balance of security and convenience.
Two Factor Authentication vs otp

Two Factor Authentication (2FA) and One-Time Password (OTP) are related concepts but have very distinct differences:
Two Factor Authentication (2FA): This is a security measure that requires users to provide two different types of verification to access an account or system. These strands fall into three categories: something the user knows (e.g password), something the user has (e.g mobile device), or something the user is (e.g biometric traits). By combination of these two strands, 2FA adds an extra coating of security to the authentication process. It aims to also protect against unauthorized access even if one factor, such as a password, is compromised.
One-Time Password (OTP): This is a specific method used within Two-Factor Authentication. It is a unique, single-use password that is generated for a specific session or transaction. OTPs are mainly time-based or event-based, meaning they are valid for a limited period of time or until they are used. OTPs can be sent via SMS, email, or generated by a dedicated authentication app. Users must enter the OTP alongside their regular password during the authentication process to verify their identity.
In essence, OTP is one of the methods used to implement two factor authentication. It provides an additional strand in the form of a unique password that expires after a single use or a certain period of time. OTPs are widely used as a convenient and secure way to add an extra coating of authentication, especially when combined with another factor like a password.
Two Factor Authentication vs password manager
The two Factor Authentication (2FA) and password managers are both important tools for enhancing security, but they serve different purposes and address different aspects of security:
Two Factor Authentication (2FA): this adds an extra coating of security to the authentication process by requiring users to provide two different types of verification. This majorly involves combining something the user knows (e.g password) with something the user has ( mobile device). 2FA helps protect against unauthorized access even if passwords are compromised, as the attacker would still need the second strand to gain access. It primarily focuses on improving the security of individual accounts and preventing unauthorized access in case passwords are compromised.
Password Manager: This is a tool that securely stores and manages passwords for various accounts. It allows users to generate strong, unique passwords for each account and store them in an encrypted database. The password manager then auto-fills the passwords when needed, eliminating the need to remember multiple complex passwords. Password managers provide convenience and help mitigate the risks associated with weak passwords, password reuse, and the use of easily guessable passwords.
While they serve different purposes, 2FA and password managers can complement each other:
- Two Factor Authentication adds an additional layer of security to account logins, protecting against unauthorized access even if passwords are compromised. It is a vital security measure that should be implemented whenever possible.
- Password managers, on the other hand, focus on password management and convenience. By using a password manager, users can generate strong, unique passwords for each account and store them securely. This reduces the reliance on memory and decreases the likelihood of using weak or reused passwords.
Combining 2FA with a password manager provides a very powerful combination of security measures. It ensures that even if passwords are compromised, the attacker would still need the second factor to gain access. Additionally, a password manager helps users maintain strong and unique passwords for all their accounts without the burden of memorizing them all the time.
Read more: 802.1x Authentication: The Major Key to Network Safety
Two Factor Authentication code
For you to obtain a two factor authentication code, you to follow these steps:
- Begin the login process on the platform or service that has two factor authentication enabled.
- Enter your username or email and your password.
- Once your credentials are verified, the platform will prompt you for the Two-Factor Authentication code.
- Depending on your chosen authentication method, you may receive the code through an SMS, email, authentication app (such as Google Authenticator or Authy), or a hardware token.
- Retrieve the code from the respective source (e.g., read the SMS, check the email, or open the authentication app).
- Enter the code into the designated field on the login page.
- Complete the authentication process by submitting the code.
- If the code is valid and matches the expected code, you will be granted access to your account.
Remember that two factor authentication codes are typically time-limited and valid for a short period. It’s important to enter the code promptly before it expires.
Two Factor Authentication iPhone
For you to enable Two Factor Authentication (2FA) on an iPhone, you have tofollow these steps:

- Open your “Settings” app on your iPhone’s home screen.
- Tap on your name at the top of the Settings screen to access your Apple ID settings.
- Scroll down and select “Password & Security” or “Apple ID > Password & Security,” depending on your iOS version.
- Tap on “Turn On Two Factor Authentication.”
- Read the information provided about Two Factor Authentication and its benefits. Tap “Continue” to proceed.
- Verify your identity by answering security questions, entering your Apple ID password, or using other authentication methods specified by Apple.
- Choose whether you want to receive verification codes via SMS or have them generated by an authentication app. Select your preferred option.
- If you choose SMS, make sure the phone number displayed is correct. If necessary, tap “Add a Trusted Phone Number” to add or change your phone number.
- If you choose an authentication app, follow the on-screen instructions to download and set up the app. Apple recommends using the “Authenticator” app, but other compatible apps like Google Authenticator or Authy can also be used.
- Follow the additional prompts to complete the setup process for Two-Factor Authentication on your iPhone.
Once enabled, two factor authentication will add an extra layer of security to your Apple ID and associated services on your iPhone. Whenever you sign in to your Apple ID or perform certain actions, you will be prompted to enter a verification code generated by your chosen method (SMS or authentication app) in addition to your password.
It’s very important to note that enabling two factor authentication on your iPhone will also affect your other Apple devices using the same Apple ID, as the verification codes will be required across all devices during the login process.
Why is Two Factor Authentication important?
Two Factor Authentication is very important because it significantly enhances security by adding an extra strand of verification. It helps protect against unauthorized access even if passwords are compromised, as the attacker would still need the second factor to gain access.
How Does Two Factor Authentication work?
Two Factor Authentication works by requiring it users to provide two separate pieces of information to verify their identity. lets say for instance, after entering a password (first factor), a one-time code is sent to the user’s mobile device (second factor), which they must enter to complete the authentication process.
What are the different types of factors used in Two Factor Authentication?
The factors used in two factor authentication mainly fall into three categories: something the user knows (egpassword or PIN), something the user has (e.g mobile device or hardware token), and something the user is (e.g.biometric traits like fingerprints or facial recognition).
Can Two Factor Authentication be bypassed or hacked?
While no security measure is entirely foolproof, Two Factor Authentication significantly increases the difficulty for attackers to bypass or hack into accounts. It requires them to have access to both the user’s password and the second factor, making unauthorized access much more difficult and challenging.
Is Two Factor Authentication only for online accounts?
Two Factor Authentication is commonly used for online accounts such as email, social media, and banking. However, it can also be implemented for other systems and applications, including VPNs, workstations, and cloud-based services to ensure enhanced security.
Do I need a smartphone for Two Factor Authentication?
While smartphones are commonly used as a second factor for Two-Factor Authentication, they are not the only option. Other methods like hardware tokens, SMS-based codes, or biometric scanners can be used as the second factor, providing alternatives for those without smartphones.
Can I use Two Factor Authentication on multiple devices?
Yes, in most cases, you can use Two-Factor Authentication on multiple devices. Popular authentication apps support multiple devices, allowing users to sync their accounts across different devices for seamless and secure authentication.
What happens if I lose my second-factor device?
If you happen to lose your second-factor device, it is import to have a backup plan. Most services offer alternative methods for authentication, such as backup codes, email verification, or contacting customer support to regain access to your account.
Is Two Factor Authentication completely secure?
While the two factor authentication significantly enhances security, no security measure is 100% secure. There are always a possibility of vulnerabilities or attacks. Nevertheless, implementing two factor authentication remains an essential best practice for protecting accounts and sensitive information from unauthorized access.
In Summary,
The two factor authentication is an essential tool in our everyday fight against cyber threats. By implementing this two factor authentication, individuals and cooperate organizations can strengthen the security of their digital interactions and protect their sensitive information from unauthorized access. As technology continues to advance, we can expect further advancements in two factor authentication, leading to a safer and more secure digital landscape. Embracing two factor authentication is a proactive step towards safeguarding our digital identities and maintaining peace of mind in an increasingly interconnected world.