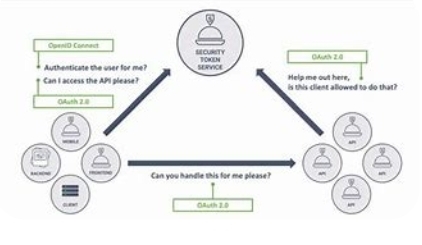
OAuth 2.0 is an open authorization protocol that allows one application to access resources on behalf of a user by obtaining an access token. It is widely used to provide secure access to third-party applications, APIs, and services.
In simple terms, OAuth 2.0 provides a framework for users to grant access to their data, without exposing their credentials to third-party applications. It helps to protect user privacy and security, by limiting the scope of access granted to third-party applications.
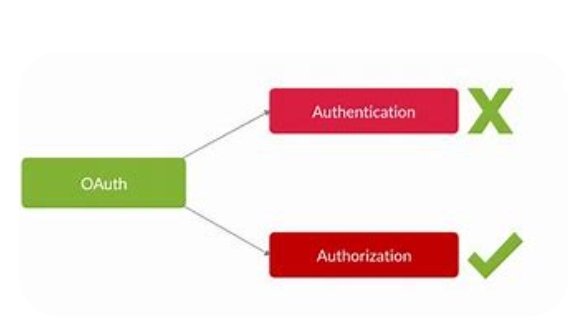
OAuth 2.0 works by separating the authentication and authorization processes. Authentication verifies the identity of the user, whereas authorization grants access to specific resources. In the case of OAuth, the authorization process involves the user granting permission to a third-party application to access their resources.

The OAuth 2.0 flow involves four parties: the user, the client application, the authorization server, and the resource server. The client application requests access to resources on behalf of the user, the authorization server grants access tokens to the client application, and the resource server provides access to resources based on the access token.
The OAuth 2.0 protocol defines several grant types, including Authorization Code Grant, Implicit Grant, Resource Owner Password Credentials Grant, and Client Credentials Grant. Each grant type provides a different way to obtain an access token, depending on the use case and security requirements.
OAuth 2.0 also provides several security features, such as scope-based consent, refresh tokens, and token revocation. Scope-based consent ensures that the user only grants access to the specific resources that the client application needs. Refresh tokens allow the client application to obtain a new access token without requiring the user to re-authenticate. Token revocation allows the user to revoke access to their resources at any time.
YOU CAN ALSO: 802.1X AUTHENTICATION: THE MAJOR KEY TO NETWORK SAFETY”.
Key OAuth 2.0 Terminology you should know
If you are new to Oauth 2.0, you probably need to know some key terminology that will help you to explore the topic perfectly. Here are ten most used Oauth terminology.
- Resource Owner: The entity that owns the resource and has the ability to grant access to the resource.
- Resource Server: The server that hosts the protected resources and can accept and respond to protected resource requests using access tokens.
- Client: The application that is requesting access to the protected resources on behalf of the resource owner.
- Authorization Server: The server that issues access tokens to the client after successfully authenticating the resource owner and obtaining authorization.
- Access Token: A token that represents the authorization granted to the client to access the protected resources.
- Refresh Token: A token that can be used to obtain a new access token when the previous one has expired without asking the user to reauthorize the client.
- Scope: A string that defines the specific authorization levels granted to the client for accessing the protected resources.
- Grant Type: The method used by the client to obtain an access token, such as authorization code, implicit, password, or client credentials.
- Redirect URI: The URI that the authorization server redirects the user’s browser to after the user successfully grants access to the client.
- Token Endpoint: The endpoint on the authorization server that the client uses to obtain access tokens and refresh tokens.
Key Features and Benefits of OAuth 2.0

OAuth 2.0 is an open standard authentication protocol that enables secure access to third-party applications without divulging important user credentials such as passwords. It is a complex framework that provides a simplified way to manage identity management for distributed systems. OAuth 2.0 offers a standardized method of web authorization that can be implemented across countless applications and platforms. In this article, we will discuss the key features and benefits of OAuth 2.0.
YOU CAN ALSO: DEFENDING YOUR DIGITAL REALM WITH TWO FACTOR AUTHENTICATION 001
Key Features of OAuth 2.0
- Simplified and streamlined authorization: OAuth 2.0 provides a simplified and streamlined process for authorization that enables users to share their information with third-party applications seamlessly.
- Enhanced Security: OAuth 2.0 offers an advanced level of security features such as encrypted tokens, SSL protection, and audience restrictions that help in protecting the user’s credentials from unauthorized access.
- Access Token-based authorization: One of the most prominent features of OAuth 2.0 is that it uses access-tokens-based authorization, which means that user credentials are never sent to third-party applications.
- Scalability: OAuth 2.0 framework is scalable in nature as it can be scaled out to accommodate high-traffic applications or distributed systems.
- Modular and adaptable: OAuth 2.0 is a modular, adaptable and extensible framework that can be customized to meet the specific needs of different applications and organizations.
- Easy integration: It is easy to integrate OAuth 2.0 into existing applications and systems such as mobile devices, web applications, and APIs.
- User-centric: OAuth 2.0 is focused on the user experience and is designed in a way that helps users to easily share their information.
Benefits of OAuth 2.0
1. Improved User Experience: OAuth 2.0 improves the user experience by enabling users to grant access to third-party applications easily.
2. Reduced Data Breach Risk: The use of tokens instead of user credentials reduces the risk of data breaches since user credentials are not shared with third-party applications.
3. Increased Security: OAuth 2.0 helps to improve the security of user data by offering advanced security features such as encrypted tokens, SSL protection, and audience restrictions.
4. Enhanced Data Control: OAuth 2.0 offers enhanced data control by enabling users to revoke access to third-party apps easily.
5. Increased Interoperability: OAuth 2.0 enables seamless interoperability between different applications and systems, reducing the need for application-specific authentication mechanisms.
6. Scalability: OAuth 2.0 is scalable and can support high-traffic applications without compromising security.
7. Enhanced Business Opportunities: OAuth 2.0 enables businesses to offer new services and expand their reach by partnering with third-party applications.
How OAuth 2.0 Works
OAuth 2.0 is an authorization protocol that allows an application to access user data from a third-party service without sharing the user’s credentials (username and password) with the application. Here is how it works:
Step 1: The user requests access to a third-party service using their account credentials (e.g. Google, Facebook, Twitter).
Step 2: The third-party service responds with an authorization code that verifies the user’s identity.
Step 3: The user’s application sends the authorization code to the third-party service’s authorization server, along with client credentials, to request an access token.
Step 4: The authorization server checks the code, and if it is valid it issues an access token.
Step 5: The application uses the access token to access the user’s data.
what are oauth 2.0 grant types
OAuth 2.0 grant types define the way in which a client application can obtain an access token from an authorization server. There are several types of OAuth 2.0 grant types which include:
- Authorization Code Grant: This grant type involves exchanging an authorization code for an access token.
- Implicit Grant: This grant type allows the client application to request access tokens directly from the authorization server without the need to exchange an authorization code.
- Resource Owner Password Credentials Grant: This grant type allows the client application to authenticate with the authorization server using the resource owner’s username and password.
- Client Credentials Grant: This grant type allows the client application to authenticate with the authorization server using its own credentials.
- Refresh Token Grant: This grant type is used to obtain a new access token using a refresh token that was previously obtained.
Each of these grant types has its own specific use case and is designed to provide different levels of security and control.
what is oauth 2.0 used for
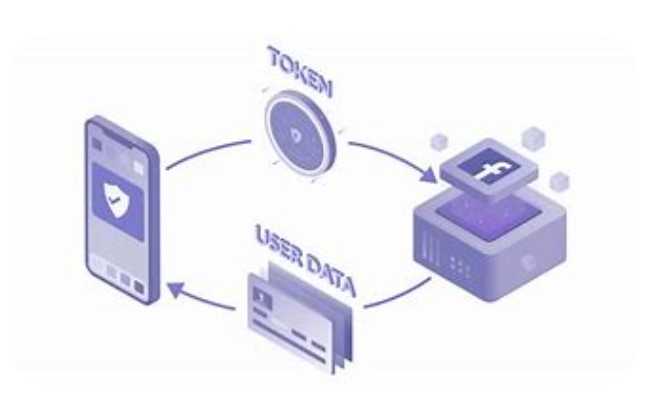
OAuth 2.0 is used for authentication and authorization purposes in web and mobile applications. It enables users to grant third-party access to their resources or data from other service providers, without sharing their credentials (i.e., username and password). OAuth 2.0 protocol can also be integrated with APIs to enable secure data exchange between various applications and services. For instance, OAuth 2.0 can be utilized for social media logins, online payment gateways, and cloud storage services.
Is oauth 2.0 secure?
Yes, OAuth 2.0 is generally considered secure when implemented correctly. It provides a framework for securely authorizing access to resources by allowing users to grant limited permissions to third-party applications without sharing their credentials. However, the security of an OAuth 2.0 implementation depends on various factors, such as the implementation quality, the use of encryption, proper authorization server configuration, and adherence to best practices. It is important to follow recommended security guidelines and stay up to date with any vulnerabilities or updates related to OAuth 2.0.
Does oauth 2.0 use saml?
No, OAuth 2.0 and SAML are two different protocols used for authentication and authorization in web applications. While they serve similar functions, they have different architectures and use different data formats. OAuth 2.0 is focused on user authorization and delegated access, while SAML is focused on user authentication and exchanging security assertions. However, it is possible to use OAuth 2.0 and SAML together in some scenarios, such as when integrating different identity providers.
YOU CAN ALSO: HOW TO KEEP YOUR WI-FI SAFE WITH WPA AUTHENTICATION PROCESS
How does oauth 2.0 work in rest api ?
OAuth 2.0 is a standard protocol widely used for authentication and authorization in REST APIs. The protocol operates through a series of interactions between the client (the application seeking access to the API), the resource owner (the user who owns the protected resources), and the authorization server (the server hosting the protected resources).
Here is a general overview of how OAuth 2.0 works in a REST API:
1. The client (an application) sends a request to access a protected resource.
2. The authorization server prompts the resource owner for consent to grant access to the client.
3. If the resource owner consents, the authorization server issues an access token, which is a unique identifier that grants limited access rights to the client.
4. The client then sends the access token to the API server with each subsequent request.
5. The API server validates the access token and, if valid, allows the client to access the requested resource.
6. When the access token expires, the client must obtain a new access token from the authorization server to continue accessing the resource.
how to use oauth 2.0 in postman

To use OAuth 2.0 in Postman, follow these steps:
1. Create a new Postman request by clicking on the ‘New’ button.
2. Set the request method, URL, and any necessary headers.
3. In the ‘Authorization’ tab, click on the ‘Type’ dropdown and select ‘OAuth 2.0’.
4. Click on the ‘Get New Access Token’ button.
5. Fill in the required fields in the ‘Get New Access Token’ popup:
a. Token Name: A name for the token.
b. Grant Type: Select the appropriate grant type for your API.
c. Callback URL: The callback URL for your API (optional).
d. Auth URL: The authorization URL for your API.
e. Access Token URL: The access token URL for your API.
f. Client ID: The client ID for your API.
g. Client Secret: The client secret for your API.
h. Scope: The scope (permissions) for your API.
i. State: A state string for your API (optional).
6. Click on the ‘Request Token’ button.
7. Once the token has been generated, click on the ‘Use Token’ button.
8. The access token will be added to the Authorization header of your request.
9. Click on the ‘Send’ button to send your request with the OAuth 2.0 authentication.
Oauth 2.0 how to refresh token
In OAuth 2.0, a refresh token is a special type of token that can be used to obtain a new access token when the current access token has expired. Refresh tokens are often used for long-lived client applications, such as mobile applications or desktop applications, where it is not practical or desirable to force the user to re-authenticate frequently.
To refresh a token using OAuth 2.0, you typically follow these steps:
1. Use your current access token to make an API call to the authorization server’s token endpoint.
2. Include your client ID, client secret, and refresh token in the request.
3. The authorization server will validate your client ID and secret, and if they are valid, will issue a new access token and, optionally, a new refresh token.
4. Use the new access token to authenticate API requests going forward.
Here is an example using the OAuth 2.0 Python library `requests_oauthlib`:
from requests_oauthlib import OAuth2Session
Define your OAuth 2.0 client credentials and refresh token
client_id = ‘YOUR_CLIENT_ID’
client_secret = ‘YOUR_CLIENT_SECRET’
refresh_token = ‘YOUR_REFRESH_TOKEN’
Create an OAuth 2.0 Session object
oauth = OAuth2Session(client_id, redirect_uri=’http://example.com/’)
Refresh the access token using the refresh token
token = oauth.refresh_token(‘https://your-authentication-server.com/token’,
refresh_token=refresh_token,
client_id=client_id,
client_secret=client_secret)
Use the new access token to make API requests
response = oauth.get(‘https://your-api.com/resource’, token=token)
Implementing OAuth 2.0

Implementing OAuth 2.0 requires careful planning and attention to security. However, by following the below steps and best practices, you can enable secure and delegated access to your application’s resources.
The following steps are involved in implementing OAuth 2.0:
- Choose a Grant Type: It supports several grant types, including Authorization Code Grant, Implicit Grant, Resource Owner Password Credentials Grant, and Client Credentials Grant. Each grant type has its own use case and security implications. Choose the grant type that best suits your application’s needs.
- Register Your Application: Before you can use the software, you need to register your application with the OAuth provider. This involves providing information such as the application name, redirect URI, and client ID/secret.
- Authentication: this requires the user to authenticate with the OAuth provider. This is typically done by redirecting the user to a login screen where they can enter their credentials.
- Authorization: After the user is authenticated, they need to authorize the application to access their resources. This involves granting specific permissions to the application.
- Token Issuance: Once the user has authorized the application, the OAuth provider issues an access token. This token is used by the application to access the user’s protected resources.
- Resource Access: With the access token, the application can now access the user’s protected resources. The token is typically sent in the Authorization header of the HTTP request.
- Token Renewal: Access tokens have a limited lifespan and expire after a certain amount of time. It provides a mechanism for renewing tokens without requiring the user to re-authenticate.
- Token Revocation: If a token is no longer needed or has been compromised, it can be revoked by the OAuth provider. This prevents unauthorized access to the user’s resources.
- Security Best Practices: When implementing, it is important to follow security best practices such as using HTTPS for all communications, validating input and output, and properly securing client IDs and secrets.
Conclusion
In summary, OAuth 2.0 is a powerful and flexible authorization protocol that enables secure access to third-party applications and services. It provides a standardized framework for user consent, access token management, and security features. It is widely used in today’s digital ecosystem, and it is essential for developers and security professionals to have a good understanding of its concepts and principles.